The Billion Dollar Computer Malware Industry
As scores of people and corporations are lining up their devices on their individual networks, the volume of personal and confidential information shared on it has grown to an best high. In the pursuit of this information, attackers have taken a renewed interest in exfiltration from both individual and corporate environments. This, in turn, has widened the telescopic of organizations vulnerable to malware-driven cybercrime. That is, in improver to banks and credit unions that are subject to online cyberbanking fraud, other organizations that are susceptible to financial frauds include,
- Insurance companies
- Payment services
- Large e-commerce companies
- Airlines
Moreover, the anatomy of set on has grown more than cohesive, and its distribution has become even more than organized. Developers of the crimeware benefit from the sale or the lease of the crimeware to the third parties who use it to perpetrate identity threat and account fraud. Today the malware manufacture supplies all the components cybercriminals require to perpetrate malware-driven crome like data theft, financial fraud, etc.
Calculator Malware Industry
(Prototype courtesy IBM software ebook)
There are multiple variants of malware existence discovered daily in the wild, capable of exploiting zero-day vulnerabilities. Some of them are designed with polymorphic capabilities. The technique circumvents signature-based detections and changes filename on each subsequent infection to escape detection. This post takes a await at the two recent forms – Ransomware & Cryptojacking.
Ransomware
In simplest terms, Ransomware is a type of malware that prevents or limits users from accessing their organisation, either past locking the system'southward screen or by locking the users' files unless a ransom is paid. It has been around for several years but has assumed more importance now in the by couple of years.
1 gene that can be attributed to the ascent of this genus of malware is the expansion of the cryptocurrencies similar Bitcoin. The modus operandi involves gaining access to a user'due south device first, encrypting of import documents/files with a primal just known to the attacker. And then, demanding transfer of funds through a currency such every bit Bitcoin or Moneypak, in substitution for the decryption of the files. In all this, the assailant places a time limit on the user to comply with the attacker'south demands following which all files are permanently deleted and therefore get untraceable, unrecoverable. Unfortunately, the most effective defence against these ransomware attacks, equally with purely destructive malware, is regular, frequent backups of systems. Without a fill-in of a compromised system, the nugget owner is at the mercy of the assailant.
Cryptojacking
Similarly, a new form of malware has emerged through malicious websites that exploit the procedure of "mining" cryptocurrencies using the processing power on the victim's computer. It'south chosen Cryptojacking. Information technology's a relatively new technique that has taken off in recent months and is more than advanced since it can generate coin from victims without ever delivering malware to their systems.
What makes malware industry a billion-dollar industry?
With the growing influence of the Internet on the daily lives of people, commerce has shifted essentially from traditional business organisation to the online platform. As a result, consumers are purchasing and selling online at a rapid pace, while revealing their personal data and financial information across the wires. Considering of this, Net, like other businesses, has established itself as a standard commercial business but has as well go a breeding footing for crime. Most a tertiary of users click on links in spam messages or malvertisements slipping into large mainstream spider web pages. Of these, one in ten users is known to accept purchased products advertised on these pages. The fact that users are buying things continues to make information technology an attractive business. The spammers fifty-fifty have their own trade associations.
Malware is widely available for purchase, therefore providing a profitable way for criminals to commit cybercrime.
Many individuals, especially youngsters go lured into this muddy business attributable to rich rewards obtained for stealing various types of information. A few examples are listed beneath.
| TYPES OF STOLEN Data | PRICE IN $ |
| Full identity information | $ 6 |
| Rich banking company business relationship credentials | $ 750 |
| US Passport information | $ 800 |
| United states of america Social Security number | $ 45 |
These prices may fluctuate in the market place depending on the supply-demand criteria.
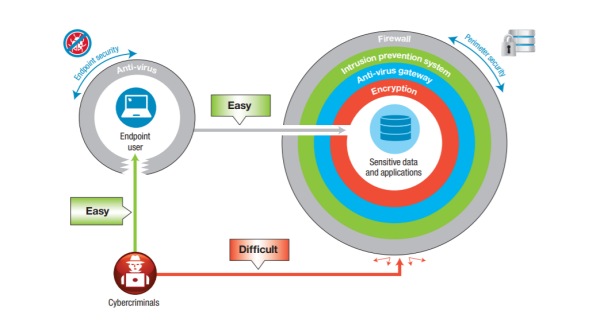
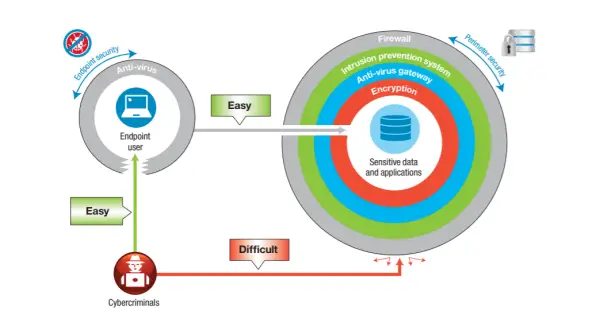
It's frequently observed that well-nigh attacks don't target the organization's systems, but rather the customer and employee endpoints. Why and so? The reason behind this is that organizations invest substantially in multiple layers of security, such equally-
- Firewalls
- Intrusion prevention systems
- Anti-virus gateways
In an attempt, to filter out cybercriminals on the perimeter. On the other manus, for endpoint security, organizations have anti-virus software in place which often detects less than 40 per centum of financial malware. As such, cybercriminals conduct malware-driven cybercrime, utilizing malware on user endpoints to commit financial fraud and steal sensitive data.
Also, if you lot know, the malware industry mainly runs Spam or Phishing malware which is written past paid professional programmers. At times, spam vendors even use professional linguists to bypass filters and psychology graduates to spam victims. There's no famine of money! Talented employees can earn in the range of $200,000 plus, per year. It gets even more rewarding for remote root zero-days $ l-100,000.
Even the workload is smartly distributed. For example, outsourcing the anti-detection code allows malware authors to concentrate on the payload.
Cyber-dacoity is on the rise and will accomplish gigantic proportions equally time passes by!
Source: https://www.thewindowsclub.com/billion-dollar-computer-malware-industry
Posted by: vegafallsocring.blogspot.com


0 Response to "The Billion Dollar Computer Malware Industry"
Post a Comment